Unfortunately for me, at the time of this writing Cellebrite UFED 4PC is unable to extract a physical image from this phone model.
After some research on the internet, I found out that there's a flasher box which is able to root specifically two Lumia phones: Lumia 800 and Lumia 800C. After rooting, according to some posts I read in the forum GSM-Forum, the phone should be recognized as a mass storage device (or something like that).
If you're not familiar with flasher boxes, I recommend you to read the article Flasher Boxes: Back to Basics in Mobile Phone Forensics. A few years ago I attended these two excellent courses in order to learn how to use these tools:
- Forensics 563: Mobile Device Forensics taught by Heather Mahalik from SANS Institute
- Flasher Box Forensics taught by Kevin Mansell from Control F
After the research phase, I needed to do some lab testing. So I bought:
- a second hand Nokia Lumia 800 (RM-801)
- Flasher box Cyclone Key Reloaded (purchased from FoneFunShop)
 |
| Cyclone Key Reloaded |
I arranged a physical machine with Microsoft Windows XP SP3. In my experience, some flasher boxes are not that stable on newer operating systems. Cyclone Key Reloaded is one of them.
Rooting the device
After installing its drivers and software, plug in the flasher box to your computer.
From the main interface of the program Cyclone Box Module Loader: click on the Nokia Tool button | go to the Connection tab | set the connection to USB.
Connect the phone to your computer (not to your flasher box) by using a standard micro USB 2.0 cable. Wait for Windows to recognize the phone.
After that:
- go to the tabs: WP7,WP8 (Qualcomm) | Simlocks
- choose RM-801 Lumia 800
- click on the ROOT ! button
This is an example log that will appear during the rooting on the right side of the program window.
[Nokia USB Connectivity]: WinUSB Port opened OK! Product code read OK Lumia No TP Root Procedure Started... If phone is alive, It will be automatically swithced to OSBL mode. If software can't switch to OSBL mode, or phone is generally DEAD do folllowing: 1. Turn OFF device, wait 15 seconds afterwards 2. Eject USB cable, wait 10 seconds 3. Press and hold Volume-UP button 4. Insert USB Cable. OSBL should be booted. Booting CMT... [Nokia USB Connectivity]: WinUSB Port opened OK! Switching to RAW Mode... [Nokia USB Connectivity]: WinUSB Port opened OK! [Nokia USB Connectivity]: WinUSB Port opened OK! OSBL Details Protocol: v1.1 Version: v257.6 Build: 12 OSBL Bootloader Ready USB&UART Tracing set RSA Signature Calculated for QCB Boot, Writing... OSBL Certificate Details Magic: WP70 Version: 0 Auth Level: Care Data Encryption: 0 Image Index: 0 Asic Index: 0 Type: Image Write Hashtable Parsed OK Certificate Accepted [ASIC 0, Storage 4,1] Writing 850.552kB @ 0x000000000007D200 Write taken 0.400s (Average speed: 17419,04kBits/s) Restoring Modem from BACKUP_RAMFS_IMAGE... Restore OK Restarting MCU... Rooting Finished!
I unplugged the phone and turned it back on. I didn't notice any data loss. All my data was still there.
Imaging the device
Go to your forensic acquisition computer.
- turn off the phone
- connect the USB cable to the computer, but not yet to the phone
- while holding the Volume Up button, connect the USB cable to the phone
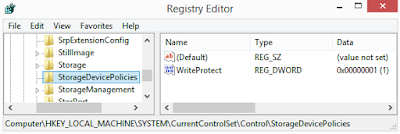
- release the Volume Up button as soon as you see Windows asking you to format the phone
- Please, don't format the device!
Now, you're ready to physically image your Nokia Lumia 800 phone.
I'll write about parsing in the next blog post.